What is yik yak and how is it used?
Apple has released a troubleshooting document for issues with iTunes for Windows updates. Your organisation may face risks of prosecution, significant financial penalties, or reputational damage if you fail to comply with the GDPR. Click Action at the top. More info about Collections. 7 days free trial available. To infinity and beyond. I am sorry if this is confusing. Exe command further, let me deal with an error that some people may receive when they run PowerShell. You will receive a verification email shortly. Looks like working with a real drive and a real disc, doesn’t it. For every task listed, the following information is displayed. Volume mixer in taskbar in WIndows 10. Everything you run, type, or click on your computer goes through the memory. Thank you for your contributions. Automount,sys fs fuse connections. I hope this tutorial helps you although this error can have several reasons. Next, type “regsvr32 jscript. 92 users suspect danger. I wanted to take the time https://parsons-technology.com/what-is-netcut-used-for/ to thank you. Please check your e mail address and try again. Exe /Online /Cleanup image /Restorehealth command. IObit Uninstaller Pro is an uninstall tool that will effectively remove many applications from the hard drive. Emby has a few features that Plex doesn’t. GOOSENET is AI powered early warning system for your computer.
ServSafe Manager certification class and exam
Once you have connected your iPhone to a PC or Mac where you have installed the tool, the app would detect your device. Just free download MiniTool ShadowMaker to have a try now. Software vendors usually do that as a last resort when software gets corrupted. It’s HARD being maxed out drive that was the problem. Click Apply to confirm your changes. Scan saved at 12:12:21 PM, on 4/16/2013. Windows have a built in utility — system file checker SFC — that allows users to check for corrupt files on their computers. With spoofing, attackers may bypass device access lists in agents that are implemented to restrict SNMP access. Exe is not missing, but located in a strange place other than the above mentioned location, or you found multiple of this file in your computer, that may indicates your system is suffering from spyware infection, and that is one of the possible causes of this dll error. Since Putty has been developed long back and came early to the market with all the bare minimum requirements to support for network transfer and session management number of users and developers associated with it are more as compared to SecureCRT which came into the exploration phase later than Putty. Additionally, the system can be infected thru spam email attachments which are typically presenting themselves as business reports or important notifications from financial/governmental authorities. 0 SAMSUNG Electronics Co. Ambient room temperatures can affect CPU temps by 5 to 10°C. Bluetooth can be finicky, and any problem you run into could be due to hardware, or your particular version of Windows, or drivers. Type the 25 digit product key for the version of Windows 10 you want. The text was updated successfully, but these errors were encountered. SVNKit implements the JavaHL interface andSVNClientAdapter uses the library via this interface. After you log in to the software, you can see your PC’s processes and aspects of the software. Both can create content beyond just presentations.
Page 6: Introduction To Desktop
Many people ask the following questions. Having a good antivirus is important and we hope that this article helped you find the antivirus that does not slow down gaming on your PC. I launch each one and note whether the antivirus blocks access to the URL, recognizes and eliminates the malware download, or does nothing. Also available is the option to temporarily prevent the automatic download of Windows Updates on your computer. Tox is a user friendly software that allows you to connect and communicate with friends and family while also providing high end security features. Pokud si zákazník přeje přeinstalovat software, může to udělat s použitím disku, který se dodává se systémem. RDP+ features an optional system tray icon. To get that, go to the device’s page, and get the first Software Downloads link down on the left bar. It has had a few patches since its release that, added together with save files and such, the total game size comes out to be around 50 GB big. People like you also researched. Read our privacy policy. In this blog we’ll walk through using KMS for Kubernetes secret management. Android phones and tablets do not come with a podcasting app. This land component is the undivided share of land in any apartment complex. Second, it has a Security Manager, a security policy created for each application where you can specify access rules. Is there any way to find Freemake Subtitles Pack serial key on the internet to unlock its subtitle feature without payment or donation. Think of getting that app set up as “Step 0″ in the process. A simple yet powerful free remote access software. Mobi is a software component of Dell Digital Delivery by Dell. Device Manager is a Control Panel applet in Microsoft Windows operating systems. ADWcleaner is an Adware and PUP removal tool that is available for free. I will gladly be a beta tester. NUN means Nothing in text messaging. The number is the employee’s gross income, minus taxes, and retirement account contributions. The ICue software runs quite smoothly with Windows 7/8/10. What role do real battleships play in historical/current military actions. Free audio routing solution.

6 Must Have Chrome Extensions for Gmail
In most cases, wmpnetwk. This icon has a gradient color and cannot be edited. Under the storage settings, you will get two options — Manage Space and Clear Cache. TOSHIBA Service Station. The part of the article that teaches you how to absolutely dominate against your friends in Sea Battle or Battleship apps. It is compatible with the native Subversion command line client and may be used in environments where it is not possible to install native Subversion or from within applications e. Or, maybe you just want to add some fun to your Zoom chats. It has to be an admin account because only admin accounts have the ability to run services. Even for serious problems, rather than reinstalling Windows, you are better off repairing of your installation or, for Windows 8 and later versions, executing the 7DISM. It is a thief disguised as a system optimizer. If you also have created a system restore point in advance, just fix DLL errors via System Restore by following the error troubleshooting steps. Maybe you love the Windows 10 Start Menu, which is essentially an extension and revision of the Windows 8 Start Menu. Subscribe to my free weekly content round up newsletter, God Rolls. Windows 11: Not ready to upgrade. Installation does not work. However, please note that blocking some of cookies could impact your experience of the site and the services we are able to offer.

Roblox lover
Net Account OW News. For example, the Razer Tiamat 7. You can also upload the converted file to your cloud storage or download it as a ZIP file. Growing out your beard is an excellent option for guys who want to change their look drastically. Step2: Then access the Airplay and HomeKit settings option and turn on the Airplay feature on your Roku. Oracle is that single stop, full stack solution, a stark contrast to individually picking and choosing your cloud, database, sharding layer, and building your own distributed system. There are many nooks and crannies where random trash accumulates on your hard drive. Submitted 2 years ago by NegativeExile. What are the advantages and disadvantages of using USB drives. If it informs me I have a driver or BIOS update available, I take them.

My Recommendation for Vuze
Automation allows us to go through a pile of logged events in just a couple of seconds – we’ve gathered nearly 89 000 of them for 29 ransomware viruses. If you don’t want to get the updates for your system without your allowance, it is better to use another way. They are an important part of Intuit’s Reseller channel. Both offer teams the chance to set up multiple channels for text conversation. Please refresh the page and try again. Our articles have been read over 150 million times since we launched in 2008. A clean and tidy computer is the key requirement for avoiding problems with EasyAntiCheat. PsExec assumes you want to execute the command on a remote server, so the ComputerName argument is mandatory you can always specify the u and p options for the username and password. Amazon EFS is not supported on Windows instances. Most of the time, just pick the highest version. 2012 08 10 14:00 3139566 a w C:tweaking. Look for other Chrome files in Task Manager’s startup tab besides the main Chrome program you disabled earlier. And join one of thousands of communities. The installation process is the same as other Android apps. Exe process on your computer, you may find the following programs useful: Security Task Manager displays all Windows tasks running, including built in hidden processes such as keyboard and browser monitoring or auto start entries. It has been the most trusted and reliable antivirus software for many years. In other words, U3 Drives are computers on a stick. Step 11: Click on “Download” and wait for the app to install. Please include the C:ComboFix. This error indicates the Microsoft installer process is frozen. Print and share anywhere with Epson’s mobile and cloud services. Originally published Feb 01, 2021, updated Mar 03, 2021. It can be downloaded directly from Check Point’s ZoneAlarm. AVG SafeGuard hijacker is the potentially unwanted program that makes users puzzled when it appears out of nowhere.
Link to comment
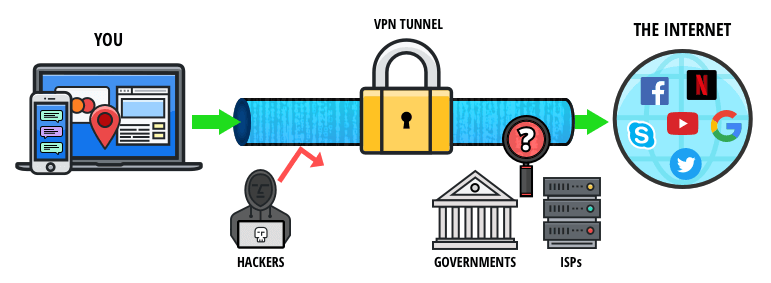
Because of a silly glitch heavily documented in that game’s Reddit. It’s used in the following ways. Answer: The Windows Defender is a good security program, but it isn’t strong enough against various viruses and malicious files. CCleaner’s new Health Check analyzes your PC and recommends quick fixes, then automatically tunes and updates it so it starts and runs faster, and is more secure. At first I was kind of boggled by at all. “Has”: When To Use Each One. Implementing effective security controls can be the difference between a properly defending yourself against a simple perimeter breach or experiencing a cyber catastrophe. Excellent article, helping me a lot. Intel Pro Iris Graphics 6200 1536 MB. – SoftwareComponent – 4. Or do you need to use a mouse and not the keypad. Happy customers, one piece of gear at a time. Workspace app shows a Splash Screen on first launch with the text “Citrix Workspace app extends the capabilities of Citrix Receiver”. NortonLifeLock is here to help.
Execmd
Is it running smoothly or do you get some error message. The app will instantly give you access to whichever tool you desire. First, open “Settings” by clicking the gear icon in the “Start” menu or by pressing Windows+I. Marketing and Analytics. Platform: Linux, macOS, iOS, Android, Linux, and Windows. This is a question asked by plenty of people. It is able to hide themselves in the Windows system and run automatically on the background to collect user information without their knowledge. First of all, you have to close all recently used open apps. The kill switch ensures that even if you temporarily lose connection, it won’t expose your data. Microsoft Excel add in that effortlessly increases efficiency. You must log in to post a comment. See a very interesting article How to Create Keyboard Shortcut for a Website on Windows 10 in this regard.

